AML Transaction Monitoring AI precision to catch more risk with less noise
Enhance risk detection with Hawk’s AML Transaction Monitoring solution. Fuse rules with AI for efficient, effective alerts, minimizing false positives. Optimize your risk management to suit your organization.

Product Differentiators Manage your AML risks effectively, without adding complexity
Gain agility and precision with self-serve rule configuration and production sandbox testing
Find more crime, slash false positives, and improve investigator speed and clarity with proven, explainable AI
Make faster, more accurate decisions with a complete understanding of each entity and their risks
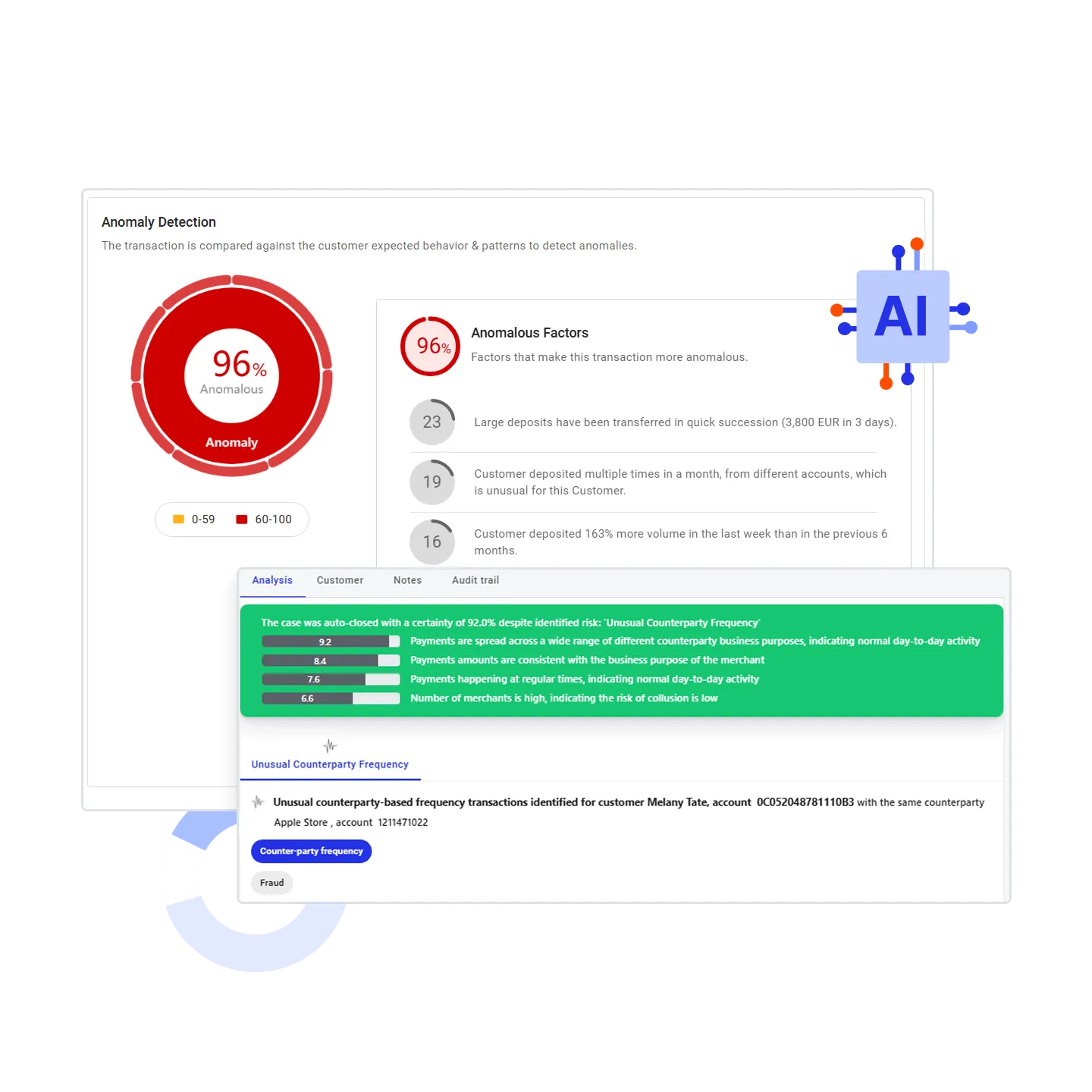
transaction monitoring software Comply with confidence
Hone in on actual money laundering activity without compromising on compliance. Hawk empowers teams with:
- Coverage of money laundering typologies, like structuring, layering and smurfing
- Monitoring of all client, product and transaction types
- Multiple layers of detection to defend against known and unknown threats, refined by AI
- Multi-tenancy to set global controls and meet regional requirements
- Pre-built investigative workflows and customer-centric investigations
- 4-eye review and model approval processes
- Automated audit trails and integrated SAR / CTR filing
AML detection Protect against illicit actors with multiple layers of defense
Protect against foundational threats
Build rules tailored to your risk profile and refine, with flexible rule templates & self-serve functionality
Increase coverage
Detects outliers & new criminal patterns. Hawk's anomaly detection builds context, assessing whether activity is truly suspicious or just a one-off before flagging for review
Cut through the noise
Reduce overall false positives, with AI that identifies common root causes for false alerts and informs triage of similar cases
Optimize over time
Gain control and improve detection accuracy with streamlined tools for model tuning and AI retraining on production data

The Hawk Difference Discover how Hawk raises the bar for transaction monitoring
The Traditional Way
- One-size-fits-all approach that doesn’t reflect local regulations
- Rules-only detection that finds more false positives than true threats
- Manual, vendor or excel-driven rule tuning on stale data
- AI that just filters already inaccurate results
- Fragmented view of a customer's risks
- Outdated user interface requiring many clicks and flipping back and forth between systems
The Hawk Way
- Multi-tenant infrastructure that supports regional regulations
- Multiple layers of defense reinforced with AI precision
- Self-serve model configuration and production data sandbox testing
- Full AI assessment of all transactions with AI explanations that drive speed and clarity
- Unified risk profile highlighting customer activities and risks flagged
- Streamlined investigations with available risk data all in one place
Awards & Recognition Leading the industry forward
Learn how Hawk's AI-fueled technology is driving the future of AML & CFT, according to software analysts and industry experts.






Agentic AI: A Practical Guide for Anti-Financial Crime and Compliance Leaders
How is agentic AI changing the way that financial crime and compliance teams work? Our latest whitepaper provides you with 50 pages of insight on the best use cases for agentic AI, covering:
- Improving investigations
- Enhancing system accuracy
- Optimizing workflows
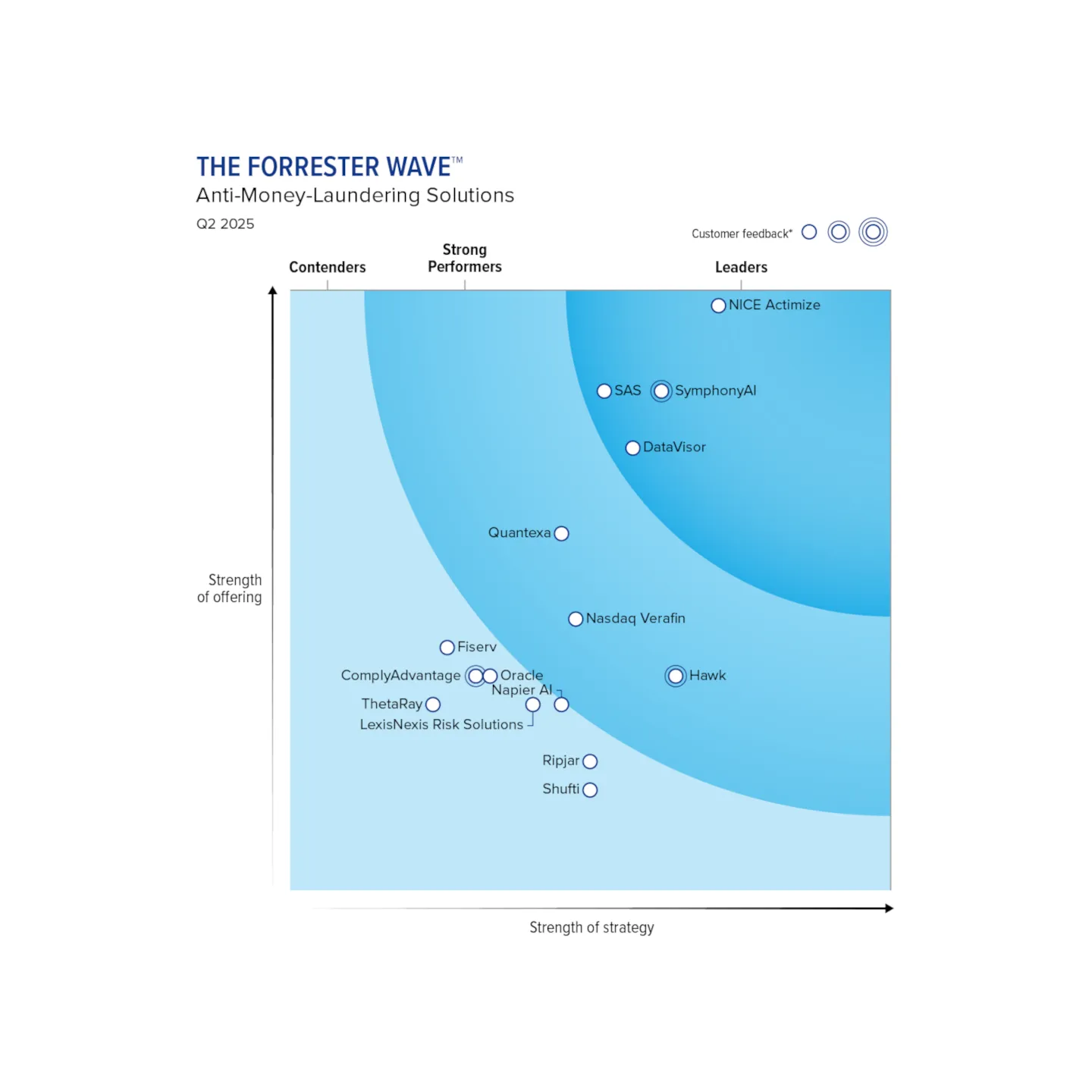
Forrester Wave Hawk Named a Strong Performer in Anti-Money Laundering Solutions Evaluation
Hawk has been recognized as a Strong Performer by Forrester in its new report “The Forrester Wave™: Anti-Money-Laundering Solutions, Q2 2025”. In the report, Forrester stated; “Hawk’s innovation is ahead of the competition.”
Frequently Asked Questions Want to know more?
Articles & Resources The latest from Hawk

Learn about the Wolfsberg Group's Statement on Effective Monitoring for Suspicious Activity, which recommends that banks move from AML transaction monitoring only to a broader approach incorporating more customer data.

Discover how Agentic AI helps financial institutions streamline the AML investigative process through data collection, case categorization, and the automated crafting of a SAR narrative.

Real-time AML has been talked about for many years. This article explores its risks, pitfalls, and the key drivers that are making real-time AML much more important today than ever before.
Request a demo Stop 2X more threats with 50% less effort with Hawk
Request a demo with one of our product experts and find out if Hawk meets your business needs.
During the demo process you'll touch on Hawk's:
- API infrastructure and data integration capabilities
- Modular design and flexible multi-tenant set up
- No-code rule builder, AI feature library, and model explanations
- Any further questions you may have